-
Remote Access Trojan For Mac카테고리 없음 2020. 2. 12. 12:54

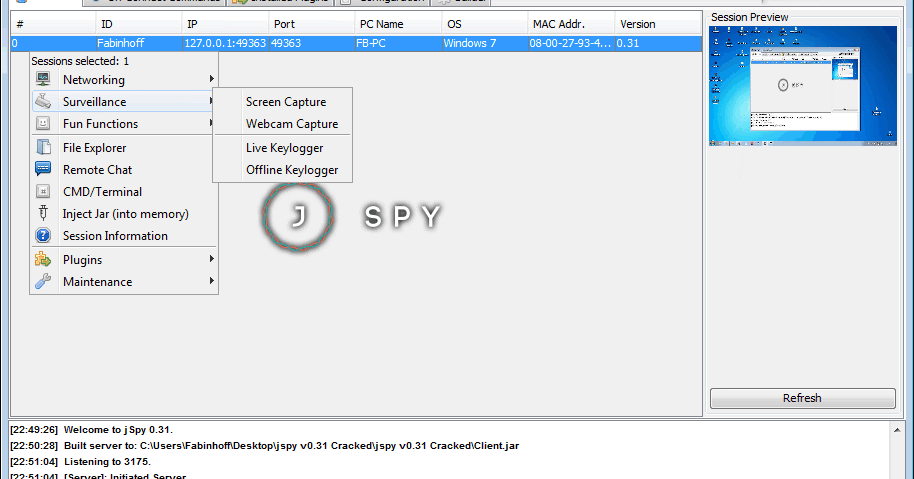
Because a RAT enables administrative control, it makes it possible for the intruder to do just about anything on the targeted computer, including:. Monitoring user behavior through or other spyware. Accessing confidential information, such as credit card and social security numbers. Activating a system's webcam and recording video. Taking screenshots. Distributing viruses and other malware.
Although security research firm Sophos wants to call the Trojan the “OSX/Musminum-A”, hackers involved prefer “Blackhole” RAT, or Remote Access Trojan.
Formatting drives. Deleting, downloading or altering files and file systems. The rootkit is one of the best known examples of a RAT. A hacker group known as the Cult of the Dead Cow created Back Orifice to expose the security deficiencies of Microsoft's Windows operating systems. RATs can be difficult to detect because they usually don't show up in lists of running programs or tasks. The actions they perform can be similar to those of legitimate programs. Furthermore, an intruder will often manage the level of resource use so that a drop in performance doesn't alert the user that something's amiss.
Remote Access Trojan For Mac Free

- A Remote Access Trojan (RAT) is a malware program that includes a back door for administrative control over the target computer. In easy language, basically, RAT is a virus which is when injected into a target computer then anyone can access that PC without Admin’s knowledge.
- Jul 7, 2016 - MAC.Eleanor and here's everything you need to know about it and keeping. Attackers to remotely access and control the infected machine.
To protect your system from RATs, follow the same procedures you use to prevent other malware infections: Keep antivirus software up to date and refrain from downloading programs or opening attachments that aren't from a trusted source. At the administrative level, it's always a good idea to block unused ports, turn off unused services and monitor outgoing traffic. RAT also stands for remote administration tool. Learn More About IT: Roger A.
Grimes wrote a comprehensive guide on how to Ed Hurley explains why.